THM - Advent of Cyber [Day 3]
This task deals with content discovery. It begins by mentioning that content includes assets and the backend of applications. Web servers serve files unless specified not to. Attackers can take advantage of this by gaining access to content that wasn’t intended to be accessed. They can gain access to config files, credentials, CMS (content management systems), etc.
This task uses dirbuster. Which is a directory brute forcing tool. I’ve used dirb a good amount, and I think it’s a good tool to use when enumerating web applications. Honestly, I feel like content discovery and fuzzing are all about a good wordlist.
The first task wants us to use dirb to enumerate the site. Here’s the syntax I use to enumerate the home directory:
dirb http://10.10.30.85/ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
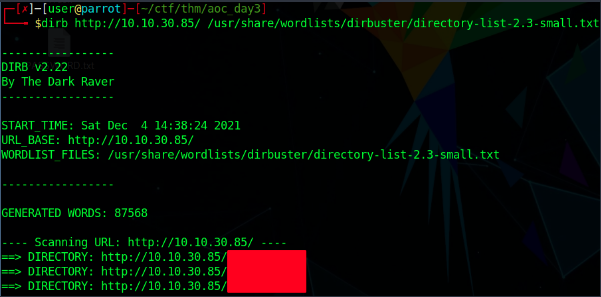
This starts the enumeration of the webpage. The brute force attack allows for us to access the admin panel. From there, we can try some typical username/password combinations to gain access and get the flag.
I’m really enjoying these bite sized ctf challenges as someone who has been out of practive and wanting to dive back in. The Advent of Cyber has also been great to demonstrate THM as a platform, with the first few days being static sites generated in browser and now using VMs that the user can access remotely.
