THM - Advent of Cyber [Day 8]
Today’s task involves the wonderful world of windows and digging through some PowerShell Transcription logs. Apparently someone at Grinch Enterprises has stolen Santa’s laptop and the only clues we have are some old PS transcription logs. I’m excited for this one because since getting my system admin job, I’ve had to work a good bit with PowerShell and I’m happy to put that to the test. I also like John Hammond’s (the creator of this room) content.
Digging Through Logs
The task mentions that you can enable PS Transcription Logs via Group Policy or by adding some registry keys. Here’s how to add the keys, just open up a PowerShell session as Administrator in case anybody feels like adding that to their own Windows Box
reg add HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\PowerShell\Transcription /v EnableTranscripting /t REG_DWORD /d 0x1 /f
reg add HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\PowerShell\Transcription /v OutputDirectory /t REG_SZ /d C:/ /f
reg add HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\PowerShell\Transcription /v EnableInvocationHeader /t REG_DWORD /d 0x1 /fConsidering this is more of a blue team exercise, we don’t have to worry about gaining any footholds or anything like that. We can just use the Windows box provided through RDP.
Digging through logs isn’t all that interesting. It’s mostly scrolling through and seeing what commands were run by the attacker. Upon a quick glance I can see the attacker made a backdoor account, downloaded some files, messed with a program, and changed some local files. I don’t want to give any screenshots since they’ll have the answer in them.
ShellBags
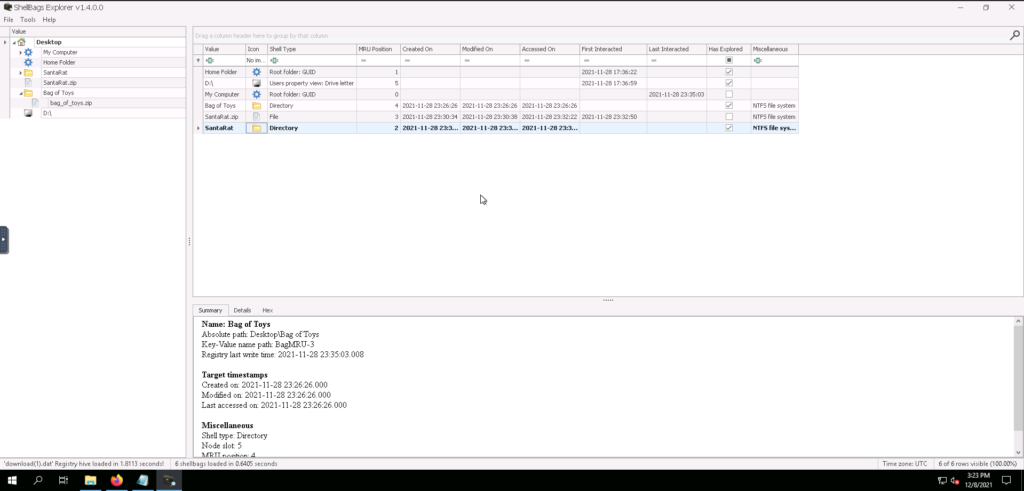
After digging through the logs, the task introduces the idea of Shellbags, which are artifacts in the windows registry that store user preferences while within the GUI. This means that directory traversal is included in Shellbags. They are located within the UserClass.dat file. Simply knowing where the Shellbags are located however is not a very useful thing, so the Windows box provided has a program called ShellBags Explorer. Before we get into ShellBags Explorer, we do need to find the part of the log that has the UserClass.dat printed to it and then de-encode it to give us the right file for ShellBags to use. This proved a little painful because the xfreerdp command that the task gave did not make the session fullscreen and Firefox was too big to show the actual recipe for cyberchef. I had to launch the session with /f to get a full screen in browser. Here’s the full command if you have the same issue:
xfreerdp /f /u:Administrator /p:grinch123! /v:IP_ADDRESS
Here’s a screenshot of ShellBags Explorer running.
OSINT
This room also involves some OSINT or Open Source Intelligence Gathering. In order to get more information on what the Grinch uploaded and how, we can take a look at his publicly available github page. There was a clue that we gathered in the ShellBag Explorer that this was a possibility.
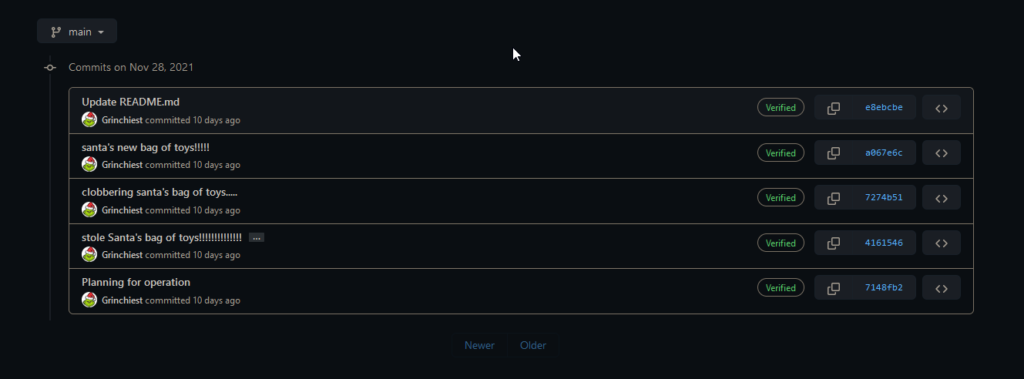
Here we can get the rest of the answers to the questions. The second to last question was a little tough because the answer is buried in the commit page that I have screenshotted above.
