THM - Advent of Cyber [Day 23]
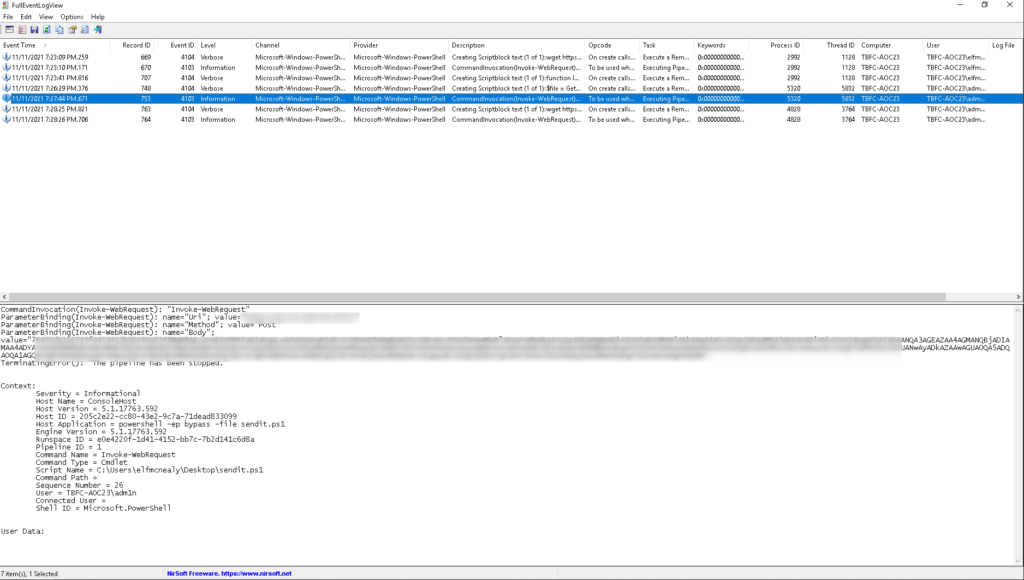
This task involves more investigation of PowerShell logging. This seems very familiar considering the Day 8 challenge was digging into PowerShell logs as well. On a normal windows box, you would go into event viewer to check out logs, but it for the purposes of this task a third party program was installed called full event log view that makes this whole operation easier.
We can specify the time, event IDs, and providers in the fields provided and search for http in the strings sections because we can assume that the attack involved web traffic. From here it’s just a matter of digging into the logs that we get back to answer all the questions.You will need to change up the search parameters to get the second to last question and the last one involves editing an existing PowerShell program and running it to get the decrypted flag.