THM - Advent of Cyber [Day 2]
This task is about web exploitation, specifically cookies and exploiting authentication through them. It talks about HTTP requests, methods, headers and of course cookies. It talks about GET requests and how those are typical when you’re loading something on a webpage. It also mentions HTML being the “language of the web”, and finally it gets into the weeds with the structure of a cookie. I liked their table that laid out the structure so here it is:
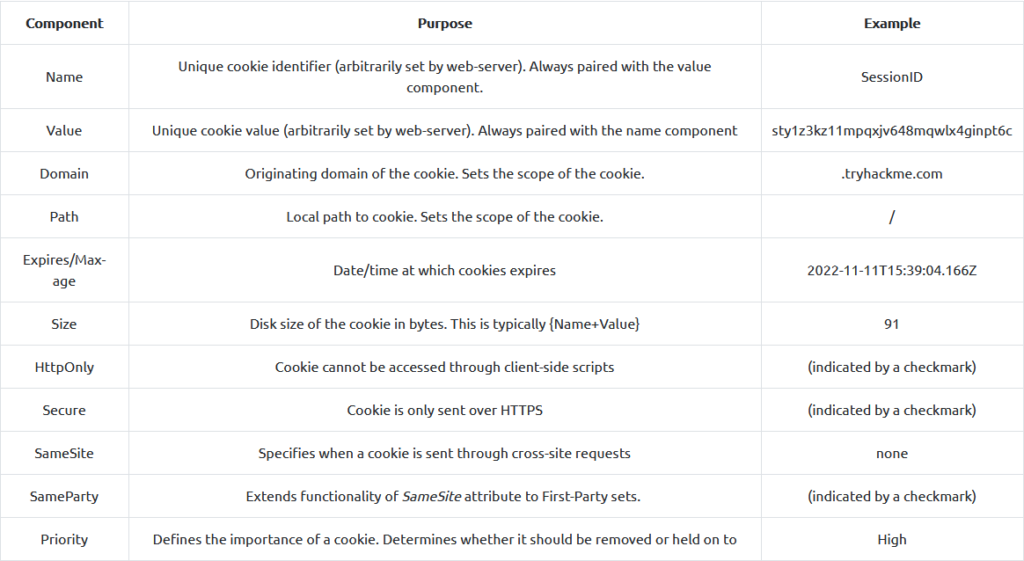
It mentions that for this room (and most ctfs in my experience) you only need to really worry about the name and value. It does also show you how cookies are built based on name-value pairs ie (<cookie name>=<cookie-value>). Cookie values can be extremely important to attackers because it can provide valuable information on specific targets. Decoding and re-encoding the key value pairs can be a potential sticking point for attackers. This task wants us to:
- Obtain a cookie by registering for an account
- Decode the cookie (might be base64)
- ID object notation (maybe xml or JSON)
- Change some parameters
- Re-encode the cookie
- Gain access to new user
As I mentioned yesterday, I like the Firefox extension Cookie Editor, which can make it super easy to view and edit cookies. That being said, you can be a 1337 hacker and use curl if you want. I’ll probably do it both ways to keep my skills up in the command line. Here’s the static site that we need to register to.
I figured the encoding would be in base64, but it wasn’t. I was on the right track with the object notation though. Once I had the cookie changed in order to authenticate as the proper user, I just had to go back to the login page and use the newly made cookie and click login to gain access to the portal. From here we can answer all the remaining questions and finish up the task!