THM - Advent of Cyber [Day 18]
today’s task, or rather yesterday’s, is about docker! I’m excited about this because my new homelab setup (writeup coming soon) relies on proxmox and docker for basically everything. I’ve been messing around a lot with docker recently, and I’m excited to not only test my current knowledge and understanding, but also learn something new!
Getting The Docker Images
This task specifically uses an AWS service to hold all it’s images. Because I do most of my tasks, including this one, on my Kali VM, I’m going to have to pull down the docker images from AWS using this command:
docker pull public.ecr.aws/h0w1j9u3/grinch-aoc:latest
Once I pull the images from AWS, I can enter into the image with this command :
docker run -it public.ecr.aws/h0w1j9u3/grinch-aoc:latest
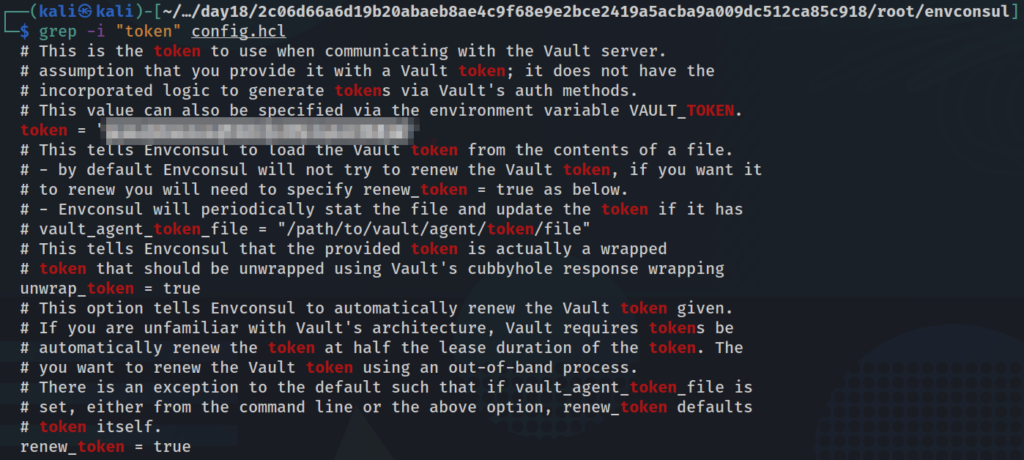
Poking around the system it doesn’t look like there’s too much happening right now, but like the task says, there’s a way that we can read what previous versions of the application looked like and maybe there was an information disclosure in another version. The first step is to download the image as tar file for further investigation.
docker save -o aoc.tar public.ecr.aws/h0w1j9u3/grinch-aoc:latest
After that we can unpack the image verbosely with the command:
tar -xfv aoc.tar
We can see all the files being unpacked, and because the format of some of the data that we’re interested in is in JSON, we can install and use the jq package to more easily read the file of interest, manifest.json. We’ll just pipe the command from cat.
cat manifest.json | jq
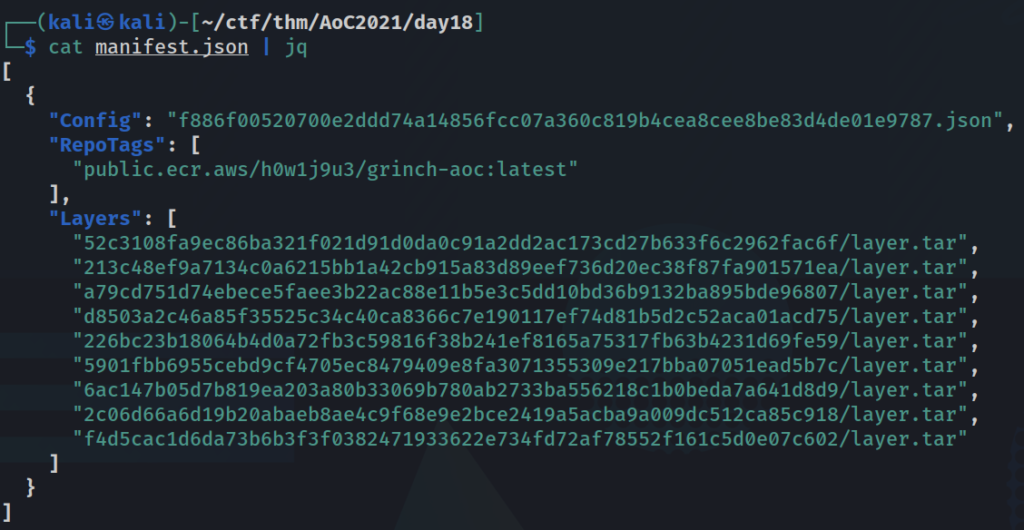
The first thing to note is the config file. This contains all the commands and configurations used to build the container. It’s also located at the root directory of our unpacked container.
If we cat out our config file with the absurdly long and random character name and pipe that through jq and scroll down a bit, we can see the commands run to build the container. Some of these commands have a key value pair of "empty_layer": true. If that pair is not there, then that layer is contained in the overall layer image listed in the manifest.json file.
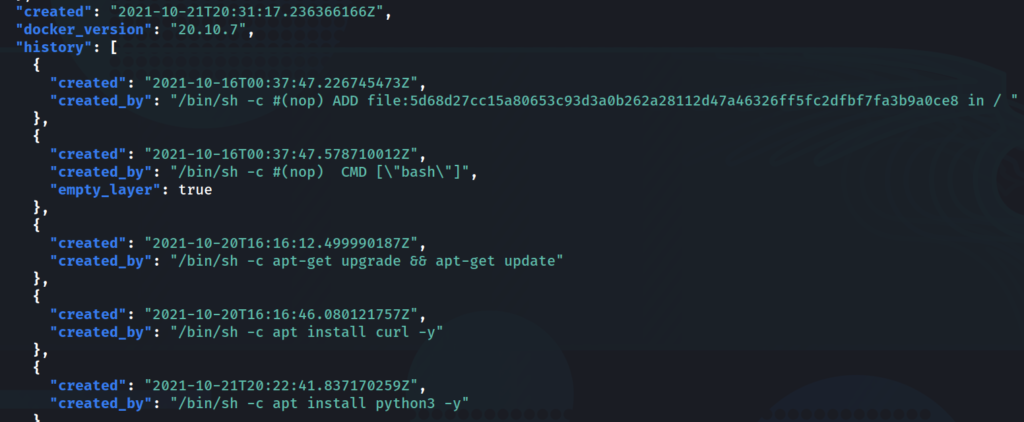
The task then instructs us that one command is pulling a repository from github, envconsul. This program may contain sensitive information. We know that by looking at the github repo for it and seeing that it may contain tokens or secrets to pull data from another source.