THM - Advent of Cyber [Day 12]
The task today involves using nmap to scan a vulnerable system, discovering an NFS share, and mounting that share so that we can access it on our attacking machine. Here’s the typical nmap scan that I use when I decide not to run threader3000:
nmap-sV -sC -T4 -Pn -oA IP_ADDR IP_ADDR
This room specifies that we need to use -Pn in order to scan the system so you can add that argument anywhere before the -oN argument.
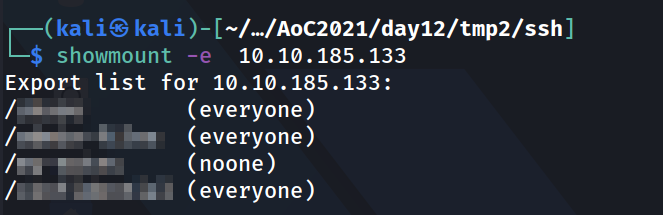
Once we figure out the port number that the NFS share is on, we can look into it by running the showmount command. We can then mount the directories to our machine and explore what’s in the NFS. We need to make a directory that we can mount the share to first. I did have to run the mount command as sudo.
mount IP_ADDR:/share tmp
From here we can cd into the directory as if it’s on our own system. The task then has us check on some basic stuff as far as files and md5 sums go. That’s pretty much it for this task. Not a whole lot to it, but still good information. You could snag ssh key and get into the system that way if you were so inclined.